With his permission it is reproduced here. The security vulnerability discovered by James Bercegay of GulfTech Security Research on the the 27th of June, , has caused quite a stir. Using the latest release of Useful Inc's php xmlrpc library, version 1. We are assuming you have already uploaded the file in your application, all you need to do is read the image file by this code. Here is a typical xml-rpc response: 
| Uploader: | Malakazahn |
| Date Added: | 6 October 2014 |
| File Size: | 52.70 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 73322 |
| Price: | Free* [*Free Regsitration Required] |
In order for livrary application to receive procedure calls coming from a remote application and respond with the needed data, it should have an HXP server created and installed. You can use the debugger to e.
WordPress XMLRPC – Posting Content From Outside WordPress Admin Panel
Note that this exploit is fixed in revisions 1. By default, the "emergency" key is either not available or set to 0 or empty character.
Click save after checking the enable box. The first security breach: The xml sent over-the-wire has ixe too with respect to some older versions of the lib in particular: There is no need to log into 20 blog accounts to post my content. A couple of new error response codes have been added, too. All use of eval has been removed since it was still a potential exploit.
XML-RPC for PHP
Mailing lists User's mailing list - very low traffic Developers' mailing list - discontinued as of December Contact For security related issues feel free to contact ggiunta at users. The number you use is pretty much up to you as the application developer, but it is important pjp keep a consistent numbering scheme.
Creating a server Creating a HXP server is very easy and straightforward by using a ready made library. Most high-profile projects have been extremely kxr in releasing new versions of their respective apps, but it will take a much longer time for every single user to update his system. A demo server is active at the address http: They both share a common ancestry, since the PEAR version is a branch of the original phpxmlrpc library, now independently maintained.
Of course, in real implementation, the function's internal routine will access the database, get the name of the patient based on the PID number which was passed as a second argument and return the name. This prevents the php scripts from using any function you deem to be unsafe, such as system or eval The hard block: The new wordpress thumbnail feature is so great, now all you have to do lubrary upload an image and mark it as featured.
These handler functions, and the array used to maintain the content of the original message, have been rewritten to construct php values instead of building php code for evaluation.

I have made a centralized Word-press control panel where i am posting blog posts in more than 20 different blogs using the same admin area. Note that this is not the same library as the one that is part of PEAR. Other libraries for other languages should have similar methods for creating the server.
XML-RPC for PHP
An attacker could easily use this as a gateway for launching viruses. I was able to get the client to execute arbitrary php code. Some internals of the lib objects changed from version 0. We are assuming you have already uploaded the file in your application, all you need to do is read the image file by this code.
It has to be said that many applications had been shipping until recently with extremely outdated versions of the phpxmlrpc library included; a first injection bug had been fixed in without anyone apparently taking notice Since the PHP engine runs under the same user as the web server, this is the first line of defense: According to some, this actually entails a "path disclosure security breach" i.
First which returns the string 'Jonathan'. I would love to hear your thoughts on this. For a complete list of changes, head on to the announcement on Github 19th of April, Released lib version 3.
Expand automatic php function to xmlrpc method wrapper to take advantage of exception handling and return xmlrpc error responses. The server exploit is just about the same as the client, except that the server is using a different eval command, and thus ph; requires slightly different begin and ending syntax to avoid php syntax errors. I was able to execute arbitrary php code, and with php's safe-mode turned off, system commands.
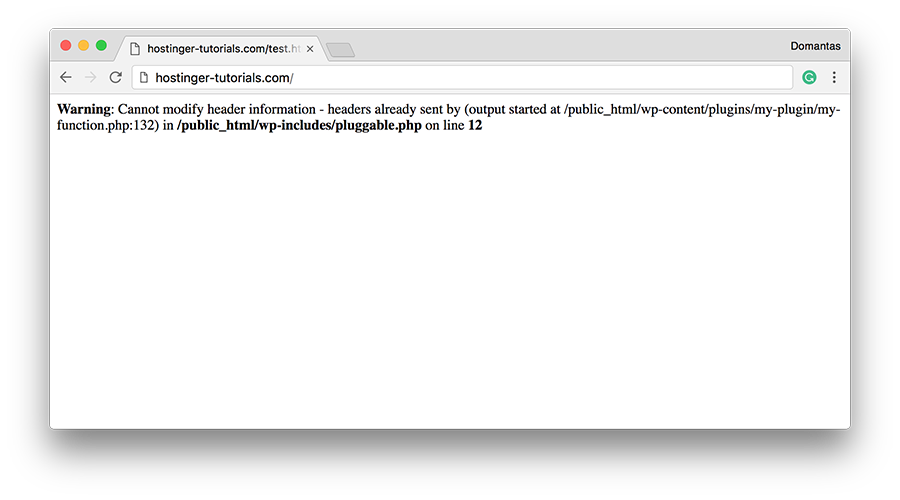
Is this the end of the world?

Comments
Post a Comment